SBOM Best Practices for DevOps Teams: Automate Software Supply Chain Security
- Ramkumar Sundarakalatharan
- Jun 30, 2025
- 4 min read
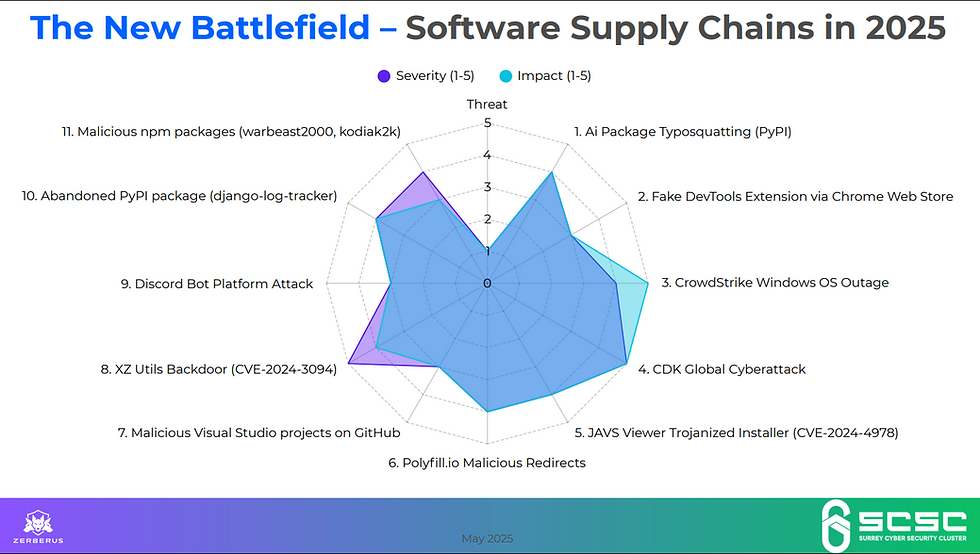
The software supply chain is under siege. In 2025 alone, we’ve witnessed a wave of sophisticated breaches — from poisoned PyPI packages to the XZ Utils backdoor that nearly compromised core Linux distributions. These attacks don’t just exploit zero-days; they exploit trust. Trust in dependencies, in package maintainers, in build systems.
SBOMs — Software Bills of Materials — are emerging as the critical response to this shifting threat landscape. When implemented correctly, SBOMs offer not only deep visibility into what you're shipping, but also provide the compliance scaffolding needed to satisfy modern standards like ISO/IEC 27001:2022, the NIST SSDF, and the EU AI Act.
At our recent Surrey Cyber Cluster session, we demonstrated live how SBOMs can be automated and operationalised inside DevOps pipelines. This post distills that session — and expands on it.
Why SBOMs Matter: The Modern Threatscape
Attackers today no longer need to breach your perimeter; they just need you to install their code.
CVE-2024-3094 / XZ Utils Backdoor: A maintainer-turned-malicious actor embedded a backdoor in a critical library, silently enabling remote SSH compromise.
JAVS Viewer Breach: Courtroom software was found shipping a tampered binary (fffmpeg.exe) with a stolen certificate.
Polyfill.io Hijack: A trusted CDN served malware to thousands of websites after domain ownership changed hands.
Each of these cases involved trust placed in upstream components — and each could have been mitigated with better metadata hygiene and traceability.
SBOMs are not a silver bullet, but they are your baseline defence.
What is an SBOM?
An SBOM is a formal, machine-readable list of components in your software — including versions, licenses, hashes, and origin metadata. Think of it as the source of truth for “what’s inside the box.”
More importantly, it allows:
CVE correlation: Are you shipping something exploitable?
License compliance: Are you unknowingly using GPL in a commercial product?
Provenance tracking: Where did this component come from? Who introduced it?
In terms of compliance:
ISO/IEC 27001:2022 – SBOMs align with controls for secure development (A.14.x), supplier relationships (A.5.19–A.5.23), and asset inventory (A.8.1).
EU AI Act – High-risk AI systems require data lineage, model provenance, and traceability.
From Theory to Pipeline: DevOps + SBOM in Action
A secure SBOM process should feel like a natural extension of your build lifecycle:
1. Build Phase
Use Syft or Trace-AI to auto-generate SBOMs.
Capture build environment, version, and hashes (SLSA Level 2 compliance).
2. Test & Validate
Grype scans SBOMs against CVE databases.
Custom rules block builds that include critical CVEs or disallowed licenses.
3. Sign & Store
Use Sigstore to sign SBOMs.
Store SBOMs next to artefacts in your container registry or artifact store.
4. Monitor & Respond
Compare SBOMs with running systems.
Feed into GUAC or internal SIEM tools to detect drift.
Case Studies: When SBOMs Could Have Made the Difference
XZ Utils Backdoor
A 3-year-long infiltration led to malicious code in a compression utility used in countless Linux systems.
An SBOM with provenance data could have flagged the sudden change in contributor pattern and dependency size.
JAVS Courtroom Installer
The use of fffmpeg.exe instead of ffmpeg.exe was caught only after major damage.
Binary diffing and verified checksums in a well-maintained SBOM would have raised alarms.
Polyfill.io Script Substitution
A harmless library used by over 100K websites started redirecting users to malicious domains.
A signed SBOM with reference hash + CDN validation could have blocked the attack early.
These aren’t hypothetical edge cases — they’re becoming common. And they’re not limited to open source. Commercial vendors are just as vulnerable.
Building a Maturity Model
Not all SBOM adoption is equal. Here’s a quick maturity model you can map your org against:
Level 0: No visibility — trust blindly
Level 1: SBOM generation post-release, no CVE triage
Level 2: Signed SBOMs + build provenance in CI/CD
Level 3: CVE gating + runtime verification
Level 4: Policy-as-code security enforcement + continuous monitoring
Aim for Level 3 as a minimum if you’re dealing with regulated industries or high-trust customers.
Toolchain Recommendations
✅ Syft – SBOM generator for container images, filesystems, and more
✅ Grype – Vulnerability scanner using SBOMs as input
✅ Sigstore – Keyless signing and transparency logs
✅ Falco – Runtime detection (great for drift from declared SBOM)
✅ GUAC – Graph queryable SBOM and SLSA ingestion engine
How Zerberus Trace-AI Helps
Trace-AI takes the manual pain out of SBOM management:
Integrates directly with CI/CD platforms
Generates SBOMs in real-time for every artefact
Signs, validates, and scans using your existing SCA and CVE feeds
Visualises lineage and flags runtime drift
Maps back to ISO 27001 and EU AI Act controls for compliance evidence
Whether you’re targeting a 10-day ISO 27001 audit or trying to land that enterprise deal, Trace-AI gives you a verifiable trust layer — without slowing your team down.
Final Thoughts + Downloadable Resource
You can’t fix what you can’t see — and that’s why SBOMs matter. They’re not just documentation. They’re a control surface, a risk lens, and your first line of defence.
Want to go deeper?
Download our extended PDF from the Surrey Cyber Cluster session:
📥 “Securing Your Software Supply Chain: A Practical Guide for Security Teams” , packed with:
Step-by-step SBOM generation
Live case analysis of 2024–2025 breaches
Quick-start toolchain checklist
Compliance mapping
The sooner you integrate SBOMs, the faster you ship secure, compliant, and trustworthy software.



Comments